Benefits
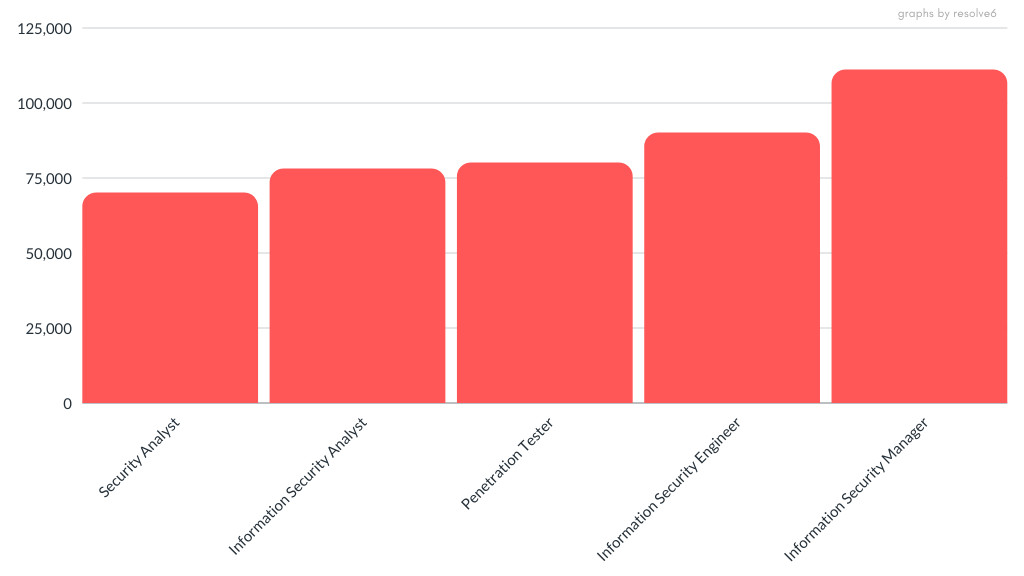
Today’s world is already entering the war of Online, or we can say the virtual world, where people don’t know how their online privacy is being violated? And how they are being used as a novice for big billions of IT companies, a terrorist group, and the government to make them richer? Here, both cyber warfare and cyber terrorism belong to the destruction world as one gets involved in a war between two countries or many. At the same time, one motivates to reach negative thoughts to promote terrorism over one community or the country targeting. So, we required more security professionals from a small startup company to the National level in the IT sector and Agriculture, telecommunications, Automobiles, Insurance Companies, and many more.
Did you know that in the next three years till 2024, around 10 million job opportunities are available worldwide, but they need subject matter expertise to secure our digital assets? So, this course was designed accordingly to enable anyone to advance their career in Cyber Security and get a good package job in the Cyber Security field. It covers all aspects from Cloud security to digital forensic to Open Source Intelligence and Penetesting Career Scope, including 4 Capstone Industrial Based Projects.
Pre-requisite: Basic Internet Knowledge and Minimal Understand of Operating System your are using (Windows, Linux or Mac)
Watch
COURSE VIDEO








Contact Us
This program is 70+ hours
Yes, interview training is included in the program. Getting our candidates ready for the interview is our key objective tagged with our skilled development
Yes, we provide on-job assistance